Reykjavik, Iceland 1986. President Reagan and USSR General Secretary Gorbachev hold their first meeting on nuclear disarmament. Reagan comes to the table “armed” with a popular Slavic saying taught to him by Russian scholar Susan Massie: “Doveryai, no proveryai” – Trust, but verify. These words become the foundation of the 1987 Intermediate-Range Nuclear Forces Treaty (INF), arguably one of the most important disarmament agreements in modern history.
In today’s volatile realm of cyber conflict, ManTech has taken “Trust but verify” to the next level: Zero Trust, a pivotal foundation for safeguarding data, IT and critical infrastructure assets vital to U.S. national and homeland security from hostile forces. Bear in mind there is no Geneva Treaty or other accord governing the conduct of cyber-enabled warfare, where foes may be found as readily in a neighboring office as across oceans and continents. As Forrester Research observes, insider threats may well drive some 33 percent of all data breaches in 2021, making Zero Trust all the more essential.
Zero Trust shifts the concept of network security and data access in a most important way: from reliance on the classic enterprise perimeter and firewall to the user/end point. In fact, long before the term itself was coined by cyber pros including Forrester analyst John Kindervag, who founded the field in 2009, Zero Trust was more commonly known as “Perimeterless” security.
The basic idea: Security must be the principal foundation of all IT systems and networks. Any kind of “trust” will always be a vulnerability.
The shift to Zero Trust represents a “sea change” from the era when devices were trusted by default. One factor in this turnaround: networks comprised of diverse, distributed infrastructure and multi-cloud environments, all accommodating mobility, the Internet of Things (IoT) and Bring-Your-Own-Device. Once breached, any perimeter-based cyber defense is open to broad control by the adversary. Another factor that makes such defenses open game for hackers: current generation AI-and bot-driven attacks – so sophisticated that they make DNS hijacks, man-in-the-middle and man-on-the-side attacks, and rootkit infections look like ancient history. Enter Zero Trust and Zero Trust Architecture (ZTA).
How Zero Trust Operates & What Sets it Apart
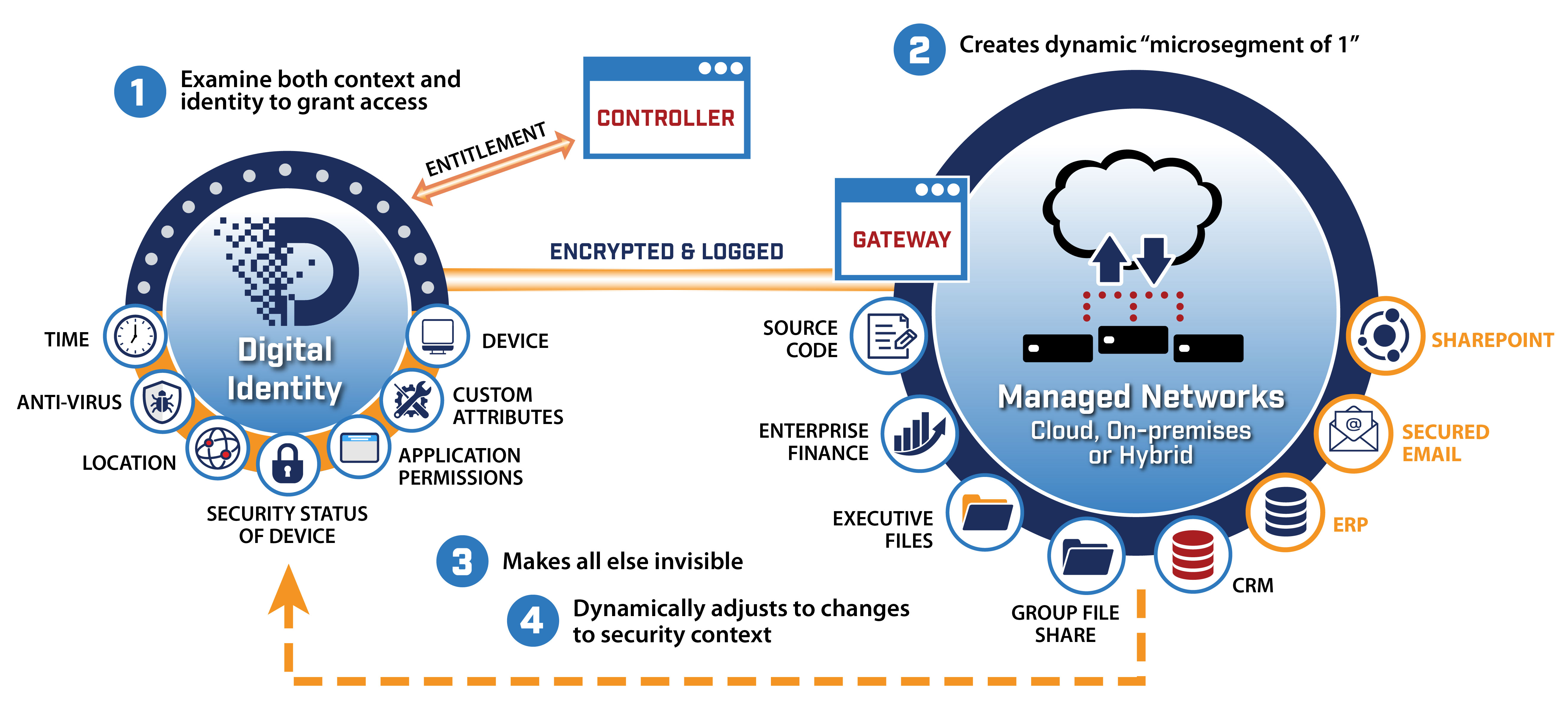
There are four basic principles, what you might call the ABCs of Zero Trust Architectures (ZTA). First, ZTA authenticates both the user and device at a granular level before granting access to the network. Second, access is granted via a dynamic microsegment, and a user working in the office on a company-provided device – or any location – is confirmed by multi-factor authentication. Third, access is confined to pre-approved destinations for that user, and all else is essentially invisible. Fourth and finally, while connected, the same user and device are continuously evaluated, and dynamic adjustments are made based on context, policy and factors that include geolocation, time and device attributes.
Among the proven benefits:
- Dramatic reduction in attack surface
- Rapid/auto response to incidents
- Improves user experience -- easy, painless
- Identity-centric device sphere view [see what you’re authenticated to see. Period]
- Telemetry-friendly to automation/AI/ML
- Scalable, Simplifies Ops, More Economical
Common use cases include VPN replacement, periodic third-party access management, protecting cloud assets or the “crown jewels” of on-premise data assets.
Myths & Reality of Implementation
Among the myths once associated with Zero Trust were that it’s a major time-eater, a significant investment, and even worse – disruptive. Those concerns have been proven wrong on each count. Access is typically granted in a matter of seconds. Deployment can be done in phases. Zero Trust significantly augments and improves security over time. And in the end, it’s cheap compared to the cost of having your system taken down.
In cybersecurity as in any field where the challenges are great, growing and continuous, one of the biggest problems is not knowing what you don’t know about potential vulnerabilities and bad actors. By authenticating users and devices non-stop and providing tightly-funneled access to micro-perimeters, you know who’s where exactly and when on your networks and infrastructure. Zero guesswork. Zero surprises. Zero Trust – one place where the value of zero adds up.